Starting my Ansible journey in the homelab, I quickly realized its potential to scale up operations for enterprise-grade offensive security. Here’s how each step unfolded:
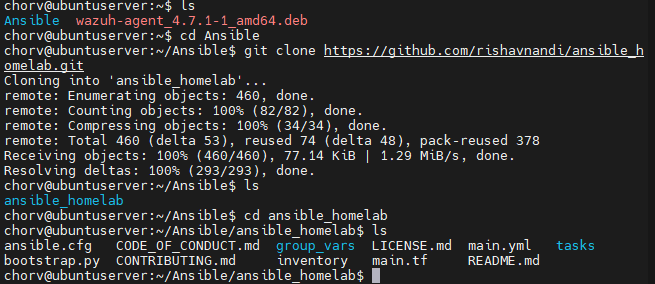
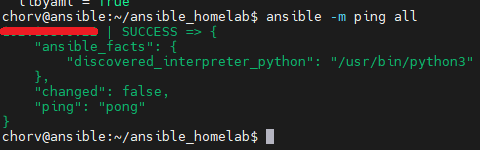
Laying a Strong Foundation and Scaling Up: My journey began with managing a single server, but Ansible’s scalability soon became apparent. It wasn’t just about server administration anymore; it was about orchestrating multiple hosts across extensive networks. This understanding, vital for enterprise IT teams, laid the groundwork for scaling operations seamlessly.
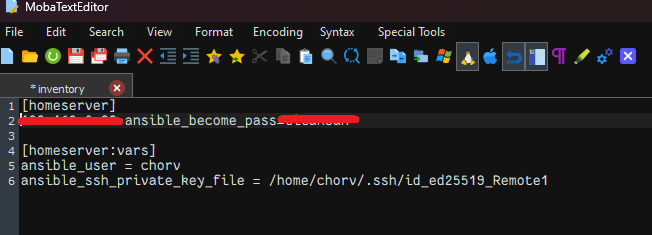
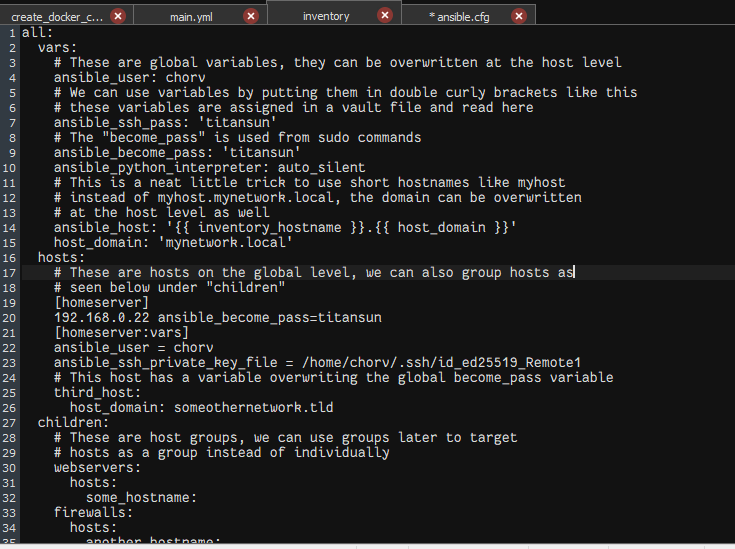
Efficiency through Automation: Discovering global variables in my playbook was a game-changer. By streamlining operations and eliminating repetitive tasks, I could ensure uniformity and enhance security—two crucial aspects for enterprises aiming for operational excellence.
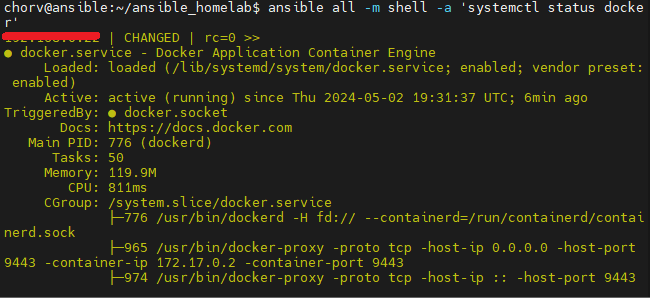
Overcoming Complex Challenges: Navigating Docker permission issues and integrating Ansible with Windows 11 were hurdles I faced. Yet, each challenge presented an opportunity for growth, enhancing my troubleshooting skills essential for handling intricate enterprise infrastructures.
Mastering Cross-Platform Proficiency: Successfully bridging Ansible across various operating systems showcased its versatility. This cross-platform capability empowered enterprises to manage diverse IT landscapes seamlessly, from Linux servers to Windows environments.
Unveiling the Potential of Security Automation: Exploring security automation revealed Ansible’s power in enforcing standards, deploying patches, and conducting vulnerability assessments. Automating these critical security processes emerged as a cornerstone for fortifying enterprise security postures.
Pioneering Offensive Security Strategies: While my focus remains on homelab automation, the potential of Ansible for offensive security is captivating. Visualizing its automation prowess within penetration testing and vulnerability assessments promises enhanced efficacy for red team engagements.
Synthesizing for Enterprise-Level Impact: Reflecting on my journey, I see Ansible as more than just a tool—it’s a strategic asset for enterprise-level offensive security. By translating homelab experiments into tangible solutions, I aim to contribute to automation initiatives, fortify security postures, and drive operational excellence across enterprises.
As I continue my journey, integrating my Synology NAS into Ansible’s ecosystem is the next step. This will streamline data management further, centralizing storage solutions and showcasing Ansible’s versatility in handling diverse infrastructure components. With this addition, I’m poised to expand my capabilities and deliver even more impactful solutions for enterprise-level offensive security.
Offensive Security Applications:
My exploration of Ansible extends beyond homelab automation. Its ability to automate tasks within penetration testing and red teaming scenarios holds immense potential for offensive security professionals. Here are some specific examples:
- Rapid Environment Setup: Playbooks can be designed to automate the configuration of Kali Linux machines, quickly deploying them with pre-installed tools and frameworks needed for specific assessments. This saves valuable time and ensures consistency across testing environments.
- Vulnerability Scanning and Exploitation: Ansible can be used to automate vulnerability scanning tools, identifying weaknesses within target systems. Additionally, playbooks can be written to exploit discovered vulnerabilities, allowing for efficient and targeted attacks.
- Post-Exploitation Activities: Once initial access is gained, Ansible can automate privilege escalation techniques, lateral movement across the network, and the deployment of persistence mechanisms. This streamlines the post-exploitation phase, enabling attackers to quickly establish control and achieve their objectives.
By mastering Ansible, you gain a powerful tool for offensive security engagements. Its automation capabilities can significantly improve efficiency, reduce human error, and enable more comprehensive and effective penetration testing.
This final addition showcases your understanding of how Ansible can be utilized beyond traditional IT automation, demonstrating its versatility and potential within the realm of offensive security.
